Cross-account access on AWS
Need a no-frills guide on cross-account access on AWS? Here it is!
Scenario Link to heading
A user in AWS Account A wants to write on an S3 bucket on Account B.
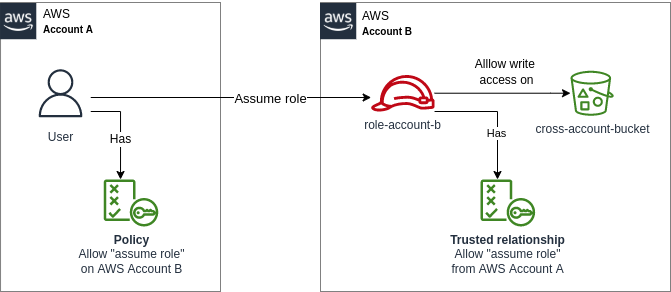
Required permissions:
- The user in Account A should be able to assume a role on the Account B
- Trust must be configured between the Account B and Account A.
How to Link to heading
In the following example: Account A has id 111111111111, Account B has id 222222222222.
-
In Account A, allow the IAM user to assume role on Account B.
{ "Version": "2012-10-17", "Statement": { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::222222222222:role/role-in-accountb" } } -
In Account B, grant access to the S3 bucket to a new role (e.g.:
role-in-accountb).{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:GetObject", "s3:PutObject", "s3:PutObjectAcl" ], "Resource": "arn:aws:s3:::222222222222/cross-account-bucket" } ] } -
In Account B, associate a trust relationship to allow users in Account A to assume the role.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::111111111111:root" }, "Action": "sts:AssumeRole" } ] }
IAM configuration can be done via AWS web console ,
Testing Link to heading
Role switch can be tested in thw AWS console via the following url.
https://signin.aws.amazon.com/switchrole?roleName=role-in-accountb&account=accountb
Do not forget to put the actual role name and account id in the query string. 😉
Role switching via AWS cli Link to heading
Assume a role via AWS CLI is also very easy. Tweak your .aws/credentials configuration as in the following example.
[accounta]
aws_access_key_id=...
aws_secret_access_key=...
[roleb]
role_arn = arn:aws:iam::222222222222:role/role-in-accountb
source_profile = accounta
Then use the new credentials as usual.
❯ aws s3 cp test.txt s3://cross-account-bucket --profile roleb
